Dive Brief:
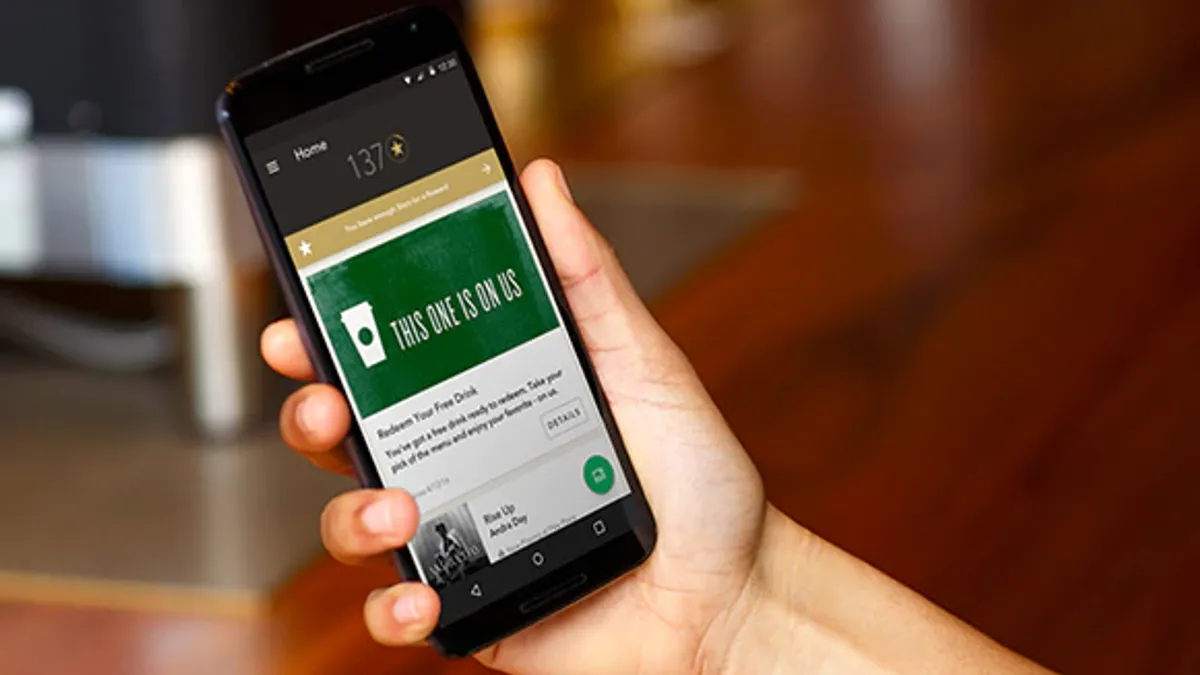
- Starbucks’ mobile application has vulnerabilities that make user accounts susceptible to hacking, Fortune magazine reported. Customers who use the same username and password on multiple sites make themselves vulnerable to hackers who gather that information from other compromised websites.
- After gaining access to a Starbucks account, a scammer can run up charges and refill the card from an attached credit card or bank account. Because gift cards can be purchased with the Starbucks app, a scammer can effectively steal cash from someone after selling the cards on the street.
- Less than 1% of Starbucks accounts have been compromised by an account takeover, the company told BuzzFeed, which said complaints about fraudulent charges are cropping up on social media.
Dive Insight:
As computer networks worldwide grapple with a massive ransomware attack that started last week, companies are reminded again of their vulnerabilities to bad actors. In the mobile arena, Starbucks is among the restaurant chains that are embracing smartphone technology with apps that can place take-out orders and make payments. About 30% of Starbucks purchases are now made with its mobile app or online, which translates into billions of dollars in sales.
Implementing two-factor authentication for mobile transactions is one way to give customers some reassurance that using an app won’t expose them to fraud. That type of authentication raises the bar for security and is common among social media applications, wireless providers and credit card issuers. It involves combining an additional factor like a unique code sent via text or answering security questions alongside the standard password input.
“Passwords are the number one security problem in the world. The only reliable defense against attackers is to enable two-factor authentication,” Corey Williams, senior director of products and marketing at cybersecurity specialist Centrify, told ITWire. He made the statement after airline booking company Sabre revealed a data breach this month.